File Integrity Monitoring
Kernel-level file monitoring with eBPF for real-time visibility, context-aware insights, and inline enforcement

Scalable File Integrity Monitoring
Security teams often face significant challenges in ensuring the integrity of critical files in their systems. Traditional file integrity monitoring (FIM) approaches, such as periodic file system scans, often miss rapid changes or fail to detect access events in real time.
These methods are prone to delays, creating a window of opportunity for malicious actors to alter or access sensitive files without detection. Additionally, monitoring systems like Inotify can struggle with scalability, expressiveness, and the ability to filter events based on specific execution contexts, such as the identity of the process accessing the file.
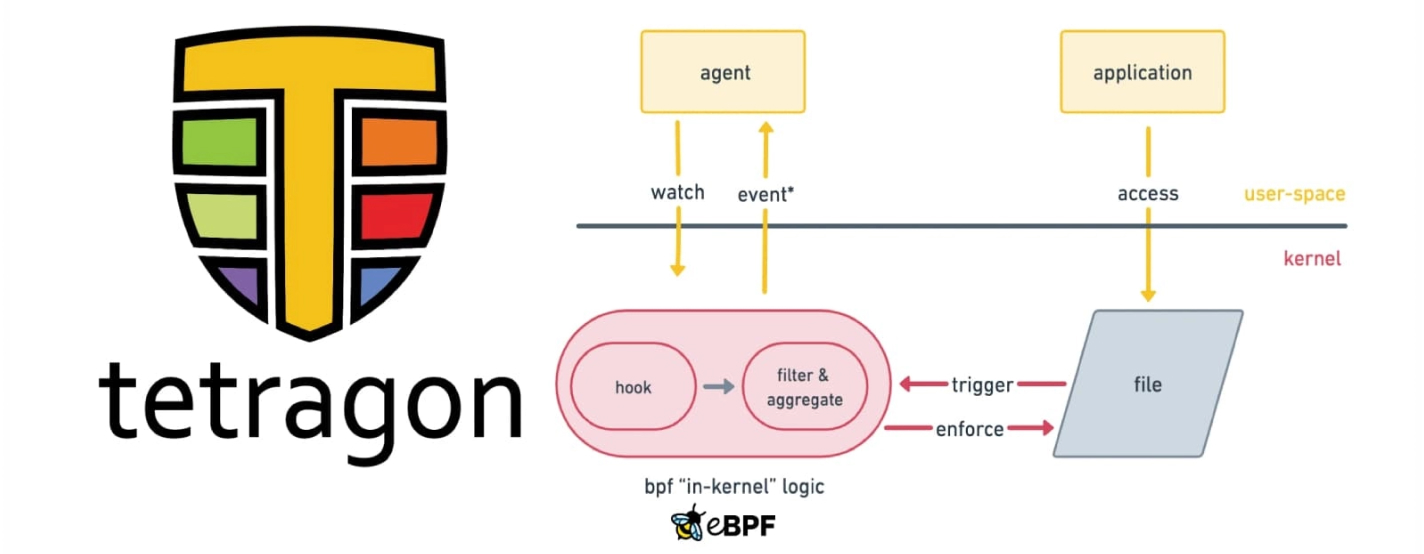
Tetragon leverages the power of eBPF to eliminate these gaps, providing a more efficient, flexible, and scalable solution for file integrity monitoring. With Tetragon, file monitoring is conducted directly in the kernel, ensuring minimal overhead and real-time visibility into file access and modification. By associating events with execution context—such as process identity and Kubernetes workload—Tetragon offers precise insights into who is accessing sensitive files and why.
Tetragon also goes beyond simple monitoring by enabling inline enforcement, allowing security teams to block unauthorized file operations at the kernel level. This advanced capability ensures that no matter how a file is accessed—whether through hard links, bind mounts, or renamed paths—Tetragon can consistently detect and respond to file changes, enabling teams to effectively respond to potential threats.
Prevent unauthorized access to resources
Real-Time File Integrity Monitoring
Monitor file access and modifications in real time with eBPF-powered kernel-level visibility.
Context-Aware Insights
Associate file events with execution context, such as process identity and Kubernetes workloads, for precise analysis.
Scalable and Flexible Monitoring
Overcome limitations of traditional FIM methods with a scalable, efficient, and expressive solution.
Inline Enforcement and Threat Response
Block unauthorized file operations at the kernel level, ensuring consistent detection and protection against malicious actions.



